In Identity Bridge, the Entitlement Configuration module allows you to manage and define templates for entitlements associated with the application. Entitlements represent the specific permissions, access rights, or privileges granted to users within the application.
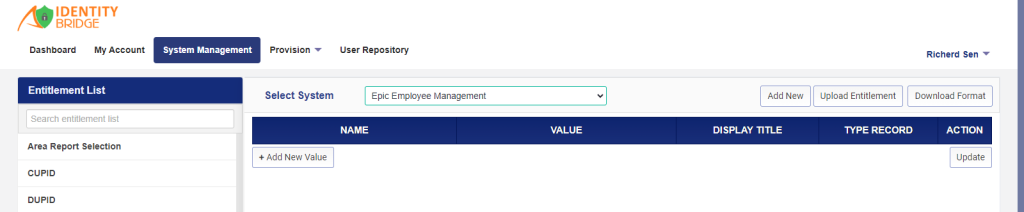
To create an entitlement, follow the steps below:
- Log in to the Identity Bridge system.
- Navigate to the System Management section.
- Find and select the Entitlement Configuration option.
- In the “Select System” dropdown, choose the name of the application you want to configure entitlements for.
- Click on the “Add New Entitlement” button. This will open a separate page for creating a new entitlement.
- On the new page, you have two options:
- Create the entitlement manually by providing the necessary values.
- Upload a CSV file containing the entitlement information. You can download the CSV file format from this page as well. If you choose to upload a CSV file, all the entitlements specified in the file will be created.
- If you decide to create the entitlement manually, enter the required values for the entitlement and click on the “Save” button.
- To edit an existing entitlement, select the application name from the “Select System” dropdown in the Entitlement Configuration section.
- This will display all the entitlement values on the main screen.
- Locate the entitlement you want to edit and click on the “pencil” icon next to it.
- Edit the necessary entitlement values and click on the “Save” button to save your changes.
Note : Entitlement Names cannot be duplicate. If user enters the Entitlement Name multiple times, all the entitlement values will get merged into a single entitlement. Entitlement values, cannot be duplicate. Duplication is based on “Encode (Name)” value.
Role of entitlement in the Identity bridge:
In Identity Bridge, entitlements play a crucial role in managing user access and permissions within an organization’s systems and applications. Here are some key aspects of entitlements in Identity Bridge:
- Access Control: Entitlements define the specific permissions and privileges that users have within an application or system. They determine what actions users can perform, what data they can access, and what functionalities they can utilize.
- Granular Permissions: Entitlements allow for fine-grained control over user access. By configuring entitlements, administrators can grant or restrict access at a detailed level, specifying which features, resources, or data sets a user is authorized to use or view.
- Role-Based Access Control (RBAC): Entitlements are often associated with roles. RBAC is a common access control model where users are assigned roles, and each role is associated with a set of entitlements. This simplifies the management of access permissions by grouping users based on their responsibilities and granting or revoking entitlements at the role level.
- Entitlement Configuration: Identity Bridge provides a user-friendly interface for configuring entitlements. Administrators can create, modify, and delete entitlements for different applications or systems within the organization. Entitlement configuration options may include specifying default access rights, defining custom permissions, and managing user groups.
- Entitlement Lifecycle Management: Identity Bridge facilitates the entire lifecycle of entitlements. This includes creating new entitlements, updating existing ones, and revoking entitlements when they are no longer needed or when user roles change. By managing entitlements centrally, organizations can ensure consistent access control across multiple applications.