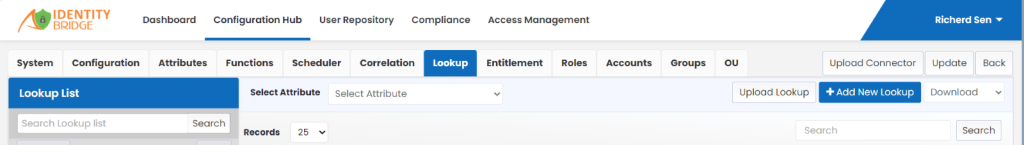
Lookup can be added by following the below process.
- Login to Identity Bridge.
- Go to Configuration Hub.
- Go to Configure Source.
- On the Active Directory Management tile click on the edit button.
- Click on the Lookup tab.
- Click Add New Lookup button.
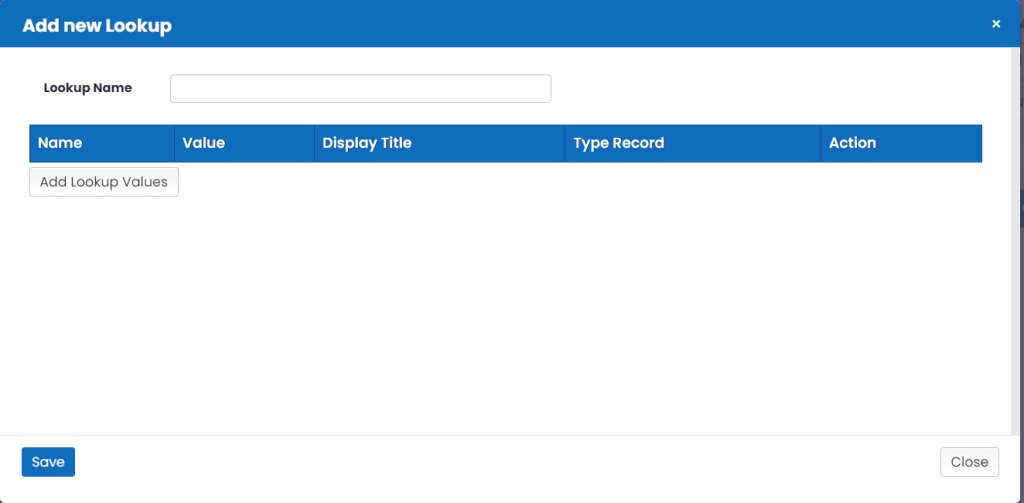
- Add new lookup window will open.
- Enter lookup name.
- Click on Add lookup values button and enter the required details.
- Click on Save button.
- To delete lookup, click on lookup then click on Bin icon.
- To upload lookup, click on Upload Lookup button.
- Upload Lookup window will open.
- Choose the file and click on Upload button.
- Click on Download arrow to download format, specific lookup or all lookup.
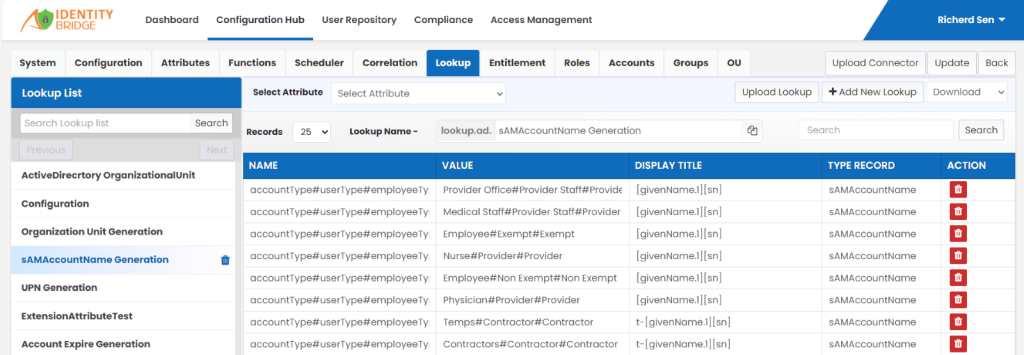
Description of Lookup Value
Below is the example of a lookup ‘SamAccountName Generation’ which contains lookup values stored in Names, Value, Display Title, Type Record and Action.
Name : accountType#user#employeeType
This is Authoritative Source System Attribute.
Value : Nurse#Provider#Provider
This is Authoritative Source System Attribute Value.
DisplayTitle : [givenName.1][sn]
User can defined its own format for SamAccountName to identify users in Active Directory, if required.
TypeRecord : sAMAccountName
This is Target System Attribute name.
Action: User can delete row if it does not exist in their system.
Identitybridge Connection and Configuration parameters are stored in the form of lookups. Additionally, lookups are used to dynamically generate data for specific attributes during provisioning based on conditions defined in the lookup table.
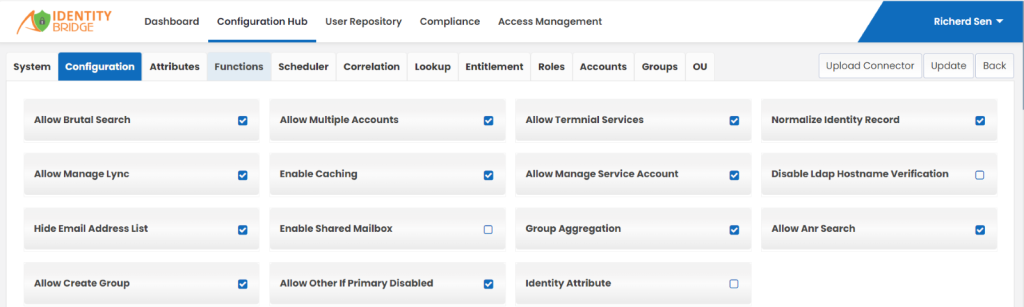
• Allow Brutal Search : Allowing brutal search means enabling a search feature that leaves no user identity unexamined. It thoroughly scans all connected systems, directories, or databases to find the specific user identity or information you’re looking for, ensuring nothing is missed. This capability can be useful for tasks like troubleshooting identity issues, auditing user accounts, or performing comprehensive searches for specific user attributes across different systems.
• Allow Manage Lync : In context of Identity Bridge, manage Lync means giving you the ability to control and manage your Lync communication software along with other applications, all from one central place.
• Hide Email Address List : In practical terms, this means configuring the identity bridge so that the email addresses of users are not visible to everyone. Only those with the proper permissions or authorization can access and view the email addresses. This helps protect the privacy of users’ email addresses and ensures they’re only shared with those who need to know.
• Allow Create Group : With this feature you can create groups of users based on common characteristics or roles, like their job departments. It helps you organize and manage users more effectively.
• Allow Multiple Accounts : Allow multiple accounts means you can create more than one account of user.
• Enable Caching : In the context of Identity Bridge, enabling caching means to store commonly accessed information. Instead of repeatedly asking other systems for the same information, identity bridge saves that information temporarily in its memory, making things faster and more efficient.
• Allow Other If Primary Disabled : Allow other if primary disabled means, if your primary account is disabled for some reason, like if it’s locked or not working properly, you can still use another account to access through this feature.
• Enable Caching : In the context of Identity Bridge, enabling caching means to store commonly accessed information. Instead of repeatedly asking other systems for the same information, identity bridge saves that information temporarily in its memory, making things faster and more efficient.
• Allow Terminal Services : In context of Identity Bridge, allow terminal services means you can use one device to connect to and control multiple devices remotely.
• Allow Manage Service Account : In the context of Identity Bridge, allow manage service account is like giving you control over these special accounts in one central place, with this enabled feature, you can easily create, modify, or delete service accounts, set their permissions, and monitor their activities across multiple applications.
• Group Aggregation : In group aggregation, Identity Bridge collects all these users from their respective groups and combines them into a single group.
• Identity Attribute : Identity Attribute defines the unique attribute in Active Directory, its a unique mapping of attribute in between Identity Bridge and AD. This is used to provision the user account in AD. Based on this attribute value Identity Bridge create, update or delete the user in AD.
• Normalize identity Record : In context of Identity Bridge, normalizing identity records means making sure that all the information about a user (like their name, email, or username) is consistent and standardized across different applications.
• Disable Ldap Hostname Verification : In practical terms, this means the identity bridge won’t verify the identity of the server it’s connecting to via LDAP (a protocol for accessing directory services). It assumes that the server is who it says it is, without double-checking.
• Allow Anr Search : Allowing ANR (Ambiguous Name Resolution) Search in terms of an Identity Bridge is like having a special search feature that can find names even if they’re not the same. It looks for matches that are similar or related, so you don’t have to type the exact name every time.
Transformation Rules/Multiple Account
Transformation rule in Identity Bridge is used to generate the user data based on the condition defined in rule. Transformation rule consumes the user data send to Identity Bridge from source. Based on attribute mapping user data get evaluated. Transformation rule can be generated or transformed.
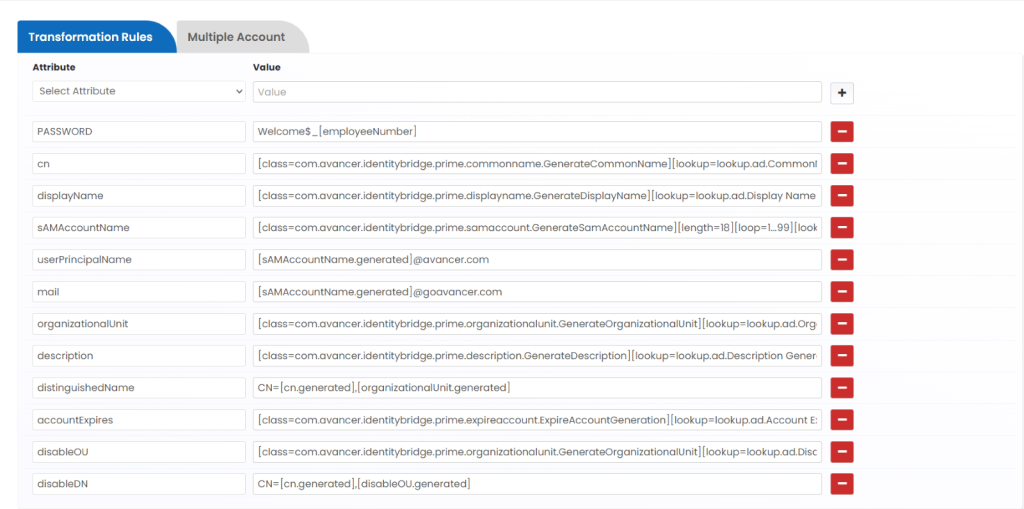
PASSWORD
Welcome$_[employeeNumber]
This example has 2 section:
- Section 1: Welcome$_
This is a hard coded string for password. This is user defined value which can include alpha numeric or special characters.
- Section2: [employeeNumber]
This is searchable AD attribute which will be [populated at runtime while generating user password.
Cn
[class=com.avancer.identitybridge.prime.commonname.GenerateCommonName][lookup=lookup.ad.CommonName Generation][replace=sAMAccountName.generated]
This example has 3 section.
- Section 1: Class is a custom java class that does specific data operation. For any changes in this class reach out to IdentityBridge team.
- Section2: Lookup here is used to generate values for CommonName based on defined conditions. Lookup can be edited in the lookup tab.
- Section 3: Replace value is passed here as the lookup in CN uses a variable of Samaccountname while generating CN.
displayName
[class=com.avancer.identitybridge.prime.displayname.GenerateDisplayName][lookup=lookup.ad.Display Name Generation]
This example has 2 section.
- Section 1: Class is a custom java class that does specific data operation. For any changes in this class reach out to IdentityBridge team.
- Section2: Lookup here is used to generate values for DisplayNameGeneration based on defined conditions. Lookup can be edited in the lookup tab.
sAMAccountName
[class=com.avancer.identitybridge.prime.samaccount.GenerateSamAccountName][length=18][loop=1…99][lookup=lookup.ad.sAMAccountName Generation]
This example has 4 section.
- Section 1: Class is a custom java class that does specific data operation. For any changes in this class reach out to IdentityBridge team.
- Section2: Length defines the length of generated SamAccountName which cannot be more than 18 characters (alpha numeric).
- Section 3: Loop handles the duplicate condition of generated SamAccountName. This condition will add number at the end or start of generated value.
- Section4: Lookup here is used to generate values for SamAccountName based on defined conditions. Lookup can be edited in the lookup tab.
userPrincipalName
[sAMAccountName.generated]@avancer.com
This is UPN of the user which cannot be modified.
[sAMAccountName.generated]@goavancer.com
This is Email for users which cannot be modified.
organizationalUnit
[class=com.avancer.identitybridge.prime.organizationalunit.GenerateOrganizationalUnit][lookup=lookup.ad.Organization Unit Generation]
This example has 2 section:
- Section 1: Class is a custom java class that does specific data operation. For any changes in this class reach out to IdentityBridge team.
- Section2: Lookup here is used to generate values for Organization Unit Generation based on defined conditions. Lookup can be edited in the lookup tab.
Description
[class=com.avancer.identitybridge.prime.description.GenerateDescription][lookup=lookup.ad.Description Generation]
This example has 2 section.
- Section 1: Class is a custom java class that does specific data operation. For any changes in this class reach out to IdentityBridge team.
- Section2: Lookup here is used to generate values for Description based on defined conditions. Lookup can be edited in the lookup tab.
distinguishedName
CN=[cn.generated],[organizationalUnit.generated]
This example is concatenation of 2 generated values separated by comma(,) as required by Active Directory.
accountExpires
[class=com.avancer.identitybridge.prime.expireaccount.ExpireAccountGeneration][lookup=lookup.ad.Account Expire Generation]
This example has 2 section.
- Section 1: Class is a custom java class that does specific data operation. For any changes in this class reach out to IdentityBridge team.
- Section2: Lookup here is used to generate values for ExpireAccountGeneration based on defined conditions. Lookup can be edited in the lookup tab.
disableOU
[class=com.avancer.identitybridge.prime.organizationalunit.GenerateOrganizationalUnit][lookup=lookup.ad.Disable Organizational Unit Generation]
This example has 2 section.
- Section 1: Class is a custom java class that does specific data operation. For any changes in this class reach out to IdentityBridge team.
- Section2: Lookup here is used to generate values for DisableOrganizationalUnit based on defined conditions. Lookup can be edited in the lookup tab.
disabledDN
CN=[cn.generated],[disableOU.generated]
This example is concatenation of 2 generated values separated by comma(,) as required by Active Directory.
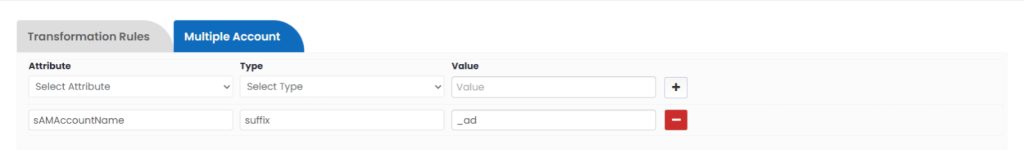
Multiple Account
Generated Samaccount will have pre-defined suffix value.
Closed Loop Remediation
Closed-loop remediation is a term that is used in Identity Management and Governance that revokes any of the access privileges of a user which were identified for revocation during a Certification process. Ideally the Closed-loop remediation feature should directly revoke roles and entitlements from the Provisioning Tool after the Certification process or campaign has flagged such entitlements of a user for revocation.
Powershell Script
Configuration tab also shows powershell script.
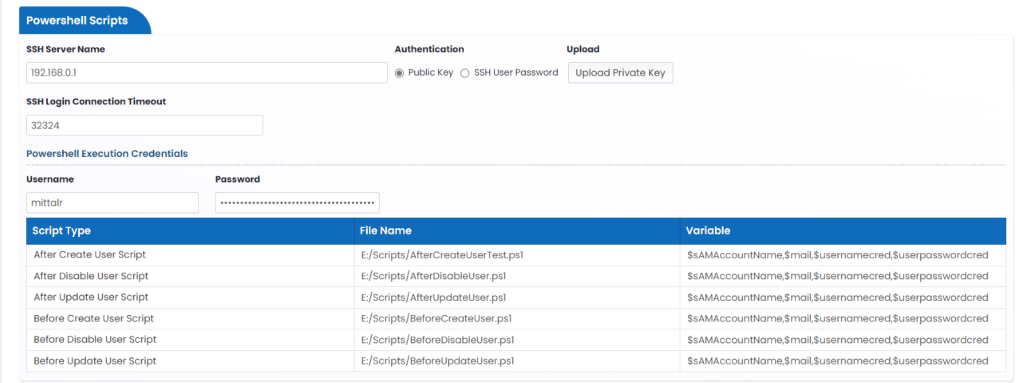
Powershell parameters – You can configure it by downloading LookUp file format or through XML file provided.
- SSH Server Name
- Connection Timeout
- Authentication
- Script Type
- Before Create User Script – This powershell script is called before creating user account
- After Create User Script – This powershell script is called after creating user account
- Before Update User Script – This powershell script is called before updating user account
- After Update User Script – This powershell script is called after updating user account
- Before Disable User Script – This powershell script is called before disabling user account
- After Disable User Script – This powershell script is called after disabling user account
- Powershell Execution Credentials (Username and password)
- File Name – Provide Powershell script complete path
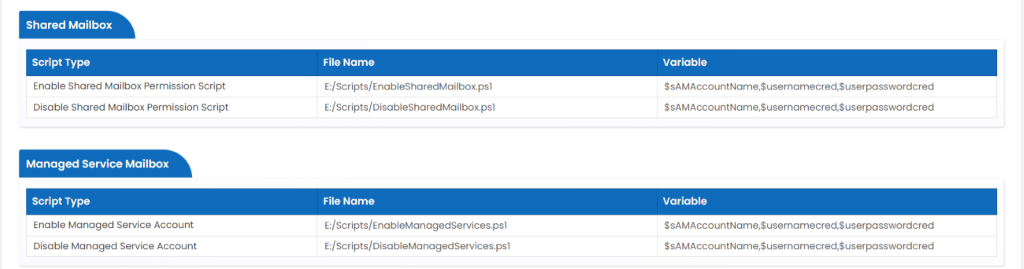
Shared Mailbox
A shared mailbox is a mailbox that multiple users can use to read and send email messages.
Upload JAR
- Click on Upload JAR tab.
- Choose the file and upload.
- This jar file contains the code, class files mentioned in the transformation rules.
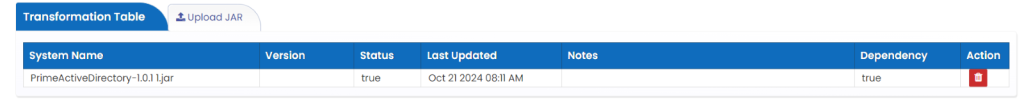
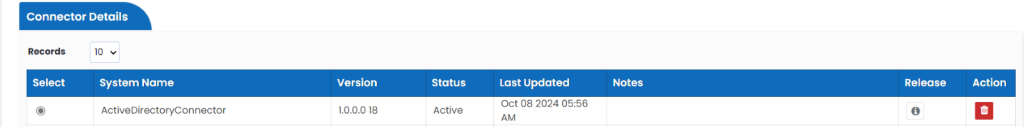
Connector Details
This shows the System Name. Version , Status and last updated date with time.